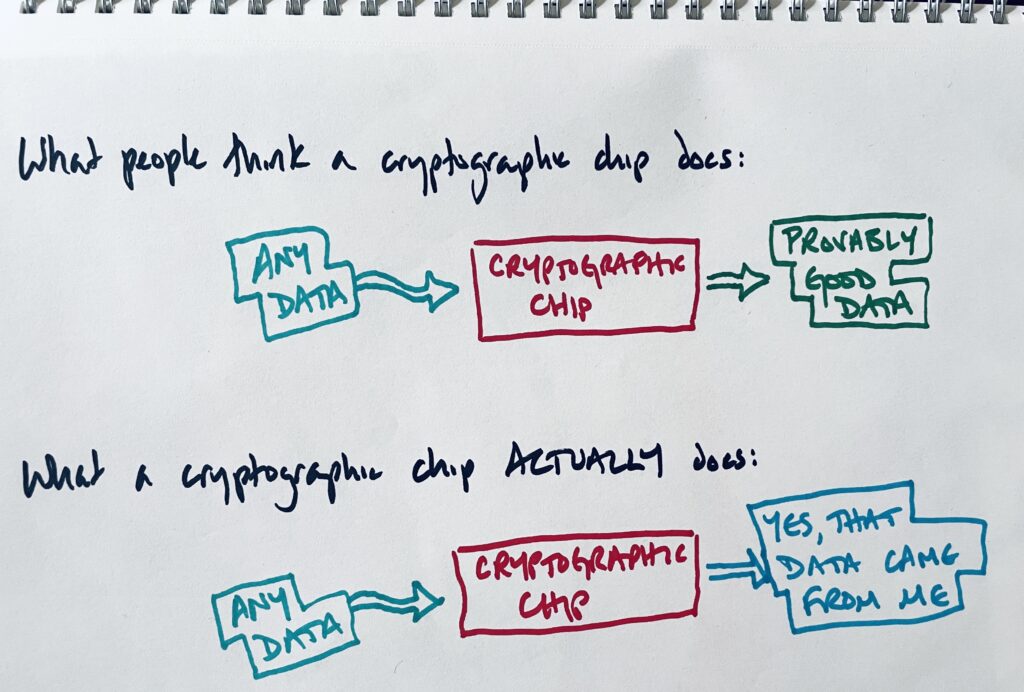
Cryptographic chips on DePIN miners are commonly thought to prove that the data from a miner is “good”.
They don’t actually do that. They just prove that the data came from a specific miner.
Slapping the word “cryptographic” on something doesn’t mean it’s automatically safer.
As GNSS expert Dr. Todd Humphreys has shown in Detection Strategy for Cryptographic GNSS Anti-Spoofing, cryptographic techniques primarily authenticate the source of the signal rather than guaranteeing the integrity of the data itself. This is a crucial distinction that has significant implications for DePIN projects.
If the data was spoofed before it got to the chip, there’s no value that the chip adds to the data.
Now, we’re not just talking about GNSS projects. This “cryptographic chip != safe” idea applies to all DePINs who think using these chips makes their project safer, or “spoof proof.”
Sometimes it’s helpful to look back at the problems that we currently face that existed before DePIN. Spoofing information is one of those problems, and the limitations of cryptographic systems in fighting it are not new.
Back in 2015, completely unrelated to DePINs or even crypto, Dr. Christina-Angeliki Toli was looking at spoofing issues where data was inserted into a system before reaching any kind of cryptographic assessment or signing.
In her paper, Provoking Security: Spoofing Attacks against Crypto-Biometric Systems, Toli highlights a key limitation of cryptography: “Cryptography can offer significant, but inadequate solutions.”
She was examining biometrics, and a fitting analogy is the classic James Bond scenario where he uses fake “gummy” fingerprints to bypass a high-tech scanner.
Even if the scanner is connected to a cryptographic system that validates the fingerprint data, cryptography can’t determine whether the fingerprints are real or fake. The data was compromised at the point of acquisition, making cryptographic validation useless.
Similarly, in DePIN systems, if data is manipulated before it reaches the cryptographic chip, no amount of cryptographic assessment will fix or reverse that. The chip can only confirm the data’s source, not its authenticity.
This happened in Helium, where sophisticated users installed software to inject “bad” data before it ever hit the crypto chip.
What Is A Crypto Chip Actually Good For?
So, what is a crypto chip actually good for, and how should you as a founder think about incorporating them? As an investor, what should you know about how crypto chips work? Are there better options than a cryptographic chip to do what it actually does?
A cryptographic chip adds costs to hardware, and it makes operations slower; they have to pass through the chip as an additional step.
While cryptographic chips do some work to ensure that the data produced is “real” (along with lots of other work that isn’t particularly useful to DePIN), what they contribute in real terms is much less of a value add for data integrity than you might think.
The paper High-Efficiency Parallel Cryptographic Accelerator for Real-Time Guaranteeing Dynamic Data Security in Embedded Systems by Zhang et al, illustrates a critical point: Maintaining security while ensuring efficiency is challenging. The study focuses on improving data security without incurring significant performance overhead. They ended up using fancy four-parallel AES-GCM hardware architecture to achieve their efficiency goals, but DePIN projects don’t have to.
A cryptographic chip’s biggest value-add in a DePIN miner is to act as a rate-limiting mechanism for how many miners can be added to a blockchain. Additional chips add a cost to every onboarded miner.
You want a rate-limiting mechanism in a DePIN so some gaming entity can’t cheaply and easily add a million miners. However, there are better mechanisms than a cryptographic chip.
If cryptographic chips don’t add much value to data integrity AND they are a cost to manufacturers with no real benefit to a DePIN, it seems that a much better way to achieve the same actual goal of rate-limiting onboarding is through onboarding fees.
As an example, one thing I observed as part of the MCC (Manufacturer’s Compliance Committee) in Helium was that a small percentage of third-party Hotspot manufacturers Hotspots were able to exploit their ability to roll keys (basically getting around the crypto chip issue totally), but they weren’t able to circumvent onboarding fees.
These bad actors were only stopped when the onboarding fee became cost-prohibitive to add more fake Hotspots at scale. The crypto chips didn’t stop them.
Onboarding fees are a much more elegant solution to the rate limiting problem. They drive value into the token rather than adding a cost. They limit the ability of a gaming entity to add large quantities of miners without paying a high cost, one that dynamically changes as demand outstrips token supply.
As DePIN continues to evolve and adapt, make sure you understand the real functions of the constituent parts.
Cryptographic chips add cost and complexity without addressing the real issue of data integrity. By shifting to a model that leverages onboarding fees and scalable incentives, founders can reduce overhead, improve data security, and increase the project’s overall capital efficiency.
If you’re building or investing in a DePIN project, consider where your resources are best allocated—toward costly hardware or adaptive, market-driven solutions that scale.
Gold Hawks & Associates LLC is a consultancy specializing in the DePIN space. We have been featured in Forbes, Fortune, and Messari and have worked with all sizes of projects including Nova Labs, Helium Foundation, Hivemapper, IoTeX, Anode Labs, Onocoy, GEODnet, WiFi Dabb, Anyone (formerly ATOR), WeatherXM, Threefold, and Eclipse Labs among others.
We assist with strategy, incentive design, and messaging. Whether you are considering starting a DePIN project or you’d like help managing your success, we stand ready to assist. Please reach out if you’d like our expertise applied to your project.
Disclaimer: Financial Interests and Consulting Services Disclosure
This blog post may contain references to various cryptocurrency projects, tokens, or assets. It is important to note that the authors of this blog post and Gold Hawks & Associates may have a financial interest in some of these projects or may provide consulting services to them, or in some cases, both.
The information and opinions expressed in this blog post are intended for informational purposes only and should not be construed as financial advice or a recommendation to invest in any specific cryptocurrency project. Readers are encouraged to conduct their own research and seek the advice of qualified financial professionals before making any investment decisions related to cryptocurrencies or any other financial assets.
The authors and Gold Hawks & Associates are committed to providing accurate and unbiased information, but it is essential to understand that our financial interests or consulting relationships with certain projects may influence the content presented. We aim to maintain transparency and integrity in our content, but readers should exercise due diligence and consider potential biases when interpreting the information provided.
Investing in cryptocurrencies involves inherent risks, and market conditions can change rapidly. It is crucial to make informed decisions and only invest funds that you can afford to lose. The authors and Gold Hawks & Associates assume no responsibility for any losses or damages resulting from actions taken based on the information presented in this blog post.
By reading and engaging with this content, you acknowledge and accept the potential conflicts of interest disclosed in this disclaimer.

Leave a Reply